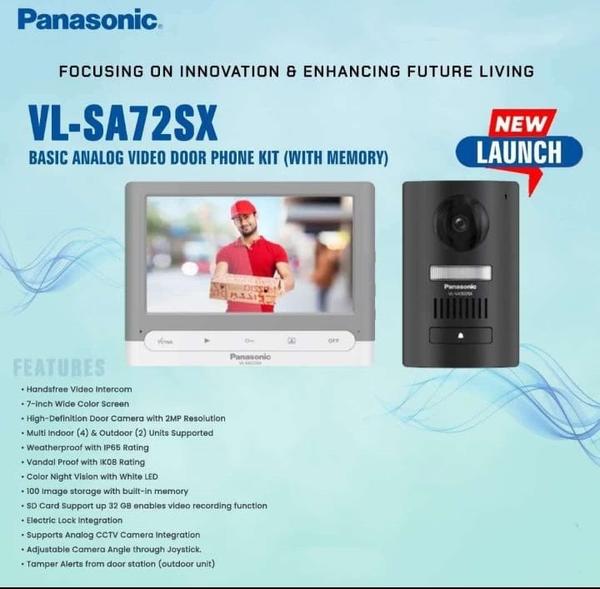
Access Control System
INR 3200 INR 3500
Enquire
Description
An Access Control System is a security solution that manages and restricts entry to a physical or digital environment. Its primary goal is to ensure that only authorized individuals can access certain areas or information. Here’s an overview of how it works and its components: Components of an Access Control System Authentication Methods: Card Readers: Use RFID cards, key fobs, or smart cards to grant access. Biometrics: Use physical characteristics like fingerprints, facial recognition, or retina scans. Keypads: Require entering a PIN or password. Mobile Credentials: Use smartphones with apps or Bluetooth for access. Access Control Panels: Controllers: Manage and process the data from authentication methods and control access to doors or other entry points. Electric Locks: Operated by the control panel to lock or unlock doors. Access Points: Doors: Controlled by the system to permit or deny access. Turnstiles and Gates: Often used in high-traffic areas. Software: Management Software: Allows administrators to set access permissions, monitor activity, and generate reports. Integration: Can be integrated with other security systems like video surveillance. Audit Trails: Logs: Record access events, including who accessed which areas and when. Types of Access Control Systems Discretionary Access Control (DAC): Ownership-based: Users have control over their own resources and can set access permissions. Mandatory Access Control (MAC): Policy-based: Access is based on security policies set by an administrator. Users cannot alter access permissions. Role-Based Access Control (RBAC): Role-based: Access permissions are assigned based on user roles within an organization. Attribute-Based Access Control (ABAC): Attribute-based: Access is granted based on attributes (such as user roles, time of day, or location). Applications of Access Control Systems Physical Security: Controlling access to buildings, rooms, or other secure areas. IT Security: Managing access to computer systems, networks, or sensitive data. Time and Attendance: Tracking employee hours and attendance. Benefits Enhanced Security: Limits access to authorized individuals only. Auditability: Provides logs for tracking access and monitoring security. Flexibility: Allows for customization of access permissions based on roles or needs. Considerations Scalability: Ensure the system can grow with your organization’s needs. Integration: Check compatibility with existing systems like CCTV or alarm systems. Maintenance: Regular updates and maintenance are needed to keep the system secure and functional. Access control systems are vital for protecting both physical and digital assets by ensuring that only authorized individuals can gain access to specific resources.